TLS1.3支持了更优秀的SSL 新特性,可以有效降低https的协商时间,建议升级
本文使用了最新的nginx 1.14.1 (该版本修正了 1.14 H2 cpu/mem 攻击漏洞: low)
#wget https://www.openssl.org/source/openssl-1.1.1.tar.gz #wget http://nginx.org/download/nginx-1.14.1.tar.gz #spdy兼容补丁 #wget https://raw.githubusercontent.com/favortel/nginx_patch/master/nginx-1.14.0_spdy_h2.patch #OKHTTP H2 头部动态压缩兼容补丁 #wget https://raw.githubusercontent.com/favortel/nginx_patch/master/fssnginx_1.14.0_dynamic_table_size.patch #PCRE ZLIB等 #wget https://ftp.pcre.org/pub/pcre/pcre-8.42.tar.gz #wget https://zlib.net/zlib-1.2.11.tar.gz #tar -zxvf openssl-1.1.1.tar.gz #tar -zxvf pcre-8.42.tar.gz #tar -zxvf zlib-1.2.11.tar.gz #tar -zxvf nginx-1.14.1.tar.gz #cd nginx-1.14.1 #patch -p1 < ../fssnginx_1.14.0_dynamic_table_size.patch #patch -p1 < ../nginx-1.14.0_spdy_h2.patch ./configure --prefix=/opt/itc/nginx --with-http_stub_status_module --with-http_realip_module --with-http_ssl_module --with-openssl=../openssl-1.1.1 --with-pcre=../pcre-8.42 --with-pcre-jit --with-zlib=../zlib-1.2.11 --with-http_v2_module --with-http_spdy_module #make && make install
配置比较简单,就是ssl_protocols 增加TLSv1.3就好, ssl_ciphers 不用特意改动:
... ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3; ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256; ssl_prefer_server_ciphers on; ssl_ecdh_curve secp384r1; ...
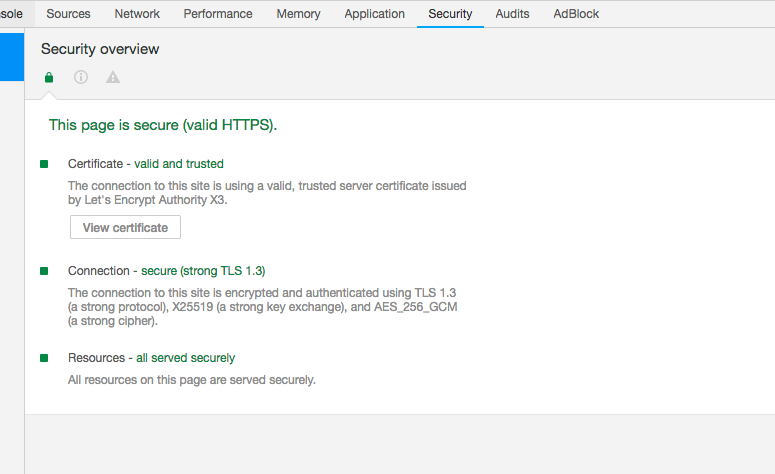
比如本站,如果您是用chrome访问的是https协议,打开开发者工具-security,就能看到本站使用了TLS1.3了